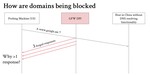
Is Nobody There? Good! Globally Measuring Connection Tampering without Responsive Endhosts
Abstract:
Many techniques have been introduced to measure network interference-tampering performed by nation-state censors or corporate …
中国の「金盾」を追跡する「GFWeb」が公開されChatGPTなどのAIサイトをいつから検閲していたのかが判明
中国政府は国内のインターネット通信を監視するため、グレートファイアウォール(金盾)という国家規模の検閲システムを運用しています。そんなグレー
New data reveals exactly when the Chinese government blocked ChatGPT and other AI sites
Rest of World received exclusive access to a platform that tracks patterns and timing of Chinese online censorship.
GFWeb provides …
GFWeb: Measuring the Great Firewall's Web Censorship at Scale
Abstract:
Censorship systems such as the Great Firewall (GFW) have been continuously refined to enhance their filtering capabilities. …
Toward Automated DNS Tampering Detection Using Machine Learning
Abstract: DNS manipulation is one of the most prevalent and effective techniques for censoring Internet access and interfering with …
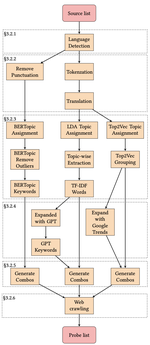
Automatic Generation of Web Censorship Probe Lists
Abstract:
Domain probe lists—used to determine which URLs to probe for Web censorship—play a critical role in Internet …
DeResistor: Toward Detection-Resistant Probing for Evasion of Internet Censorship
Abstract: The arms race between Internet freedom advocates and censors has catalyzed the emergence of sophisticated blocking techniques …
Augmenting Rule-based DNS Censorship Detection at Scale with Machine Learning
Abstract:
The proliferation of global censorship has led to the development of a plethora of measurement platforms to monitor and …
Detecting Network Interference Without Endpoint Participation
Abstract: Internet censorship research has been centered around notorious censors (e.g., China, Russia, and Iran) since they have …
Measuring and Evading Turkmenistan's Internet Censorship
Abstract: Since 2006, Turkmenistan has been listed as one of the few Internet enemies by Reporters without Borders due to its …
New study finds Internet censorship in Turkmenistan reaches over 122,000 domains
Blanket type censorship results in massive collateral damage!
The dictatorship in Turkmenistan does not get a lot of media and …
Measuring the Accessibility of Domain Name Encryption and its Impact on Internet Filtering
Most online communications rely on DNS to map domain names to their hosting IP address(es). Previous work has shown that DNS-based …
Exhaustive study puts China’s infamous Great Firewall under the microscope
China’s notorious website-blocking technology is impacting the global DNS system as well as restricting access to content locally, …
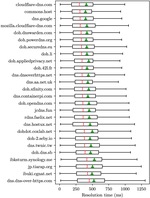
How Great is the Great Firewall? Measuring China's DNS Censorship
Abstract: The DNS filtering apparatus of China’s Great Firewall (GFW) has evolved considerably over the past two decades. …
How The Great Firewall Reflects Beijing’s Policy
The Internet censorship analyst talks about the evolution of China’s system, how it differs from and affects other countries, and …
Domain Name Encryption Is Not Enough: Privacy Leakage via IP-based Website Fingerprinting
Although the security benefits of domain name encryption technologies such as DNS over TLS (DoT), DNS over HTTPS (DoH), and Encrypted …
China suddenly blocked an Indonesian newspaper. No one knows why
Earlier this week, Chinese censors abruptly blocked access to the website of Jawa Pos, one of Indonesia’s largest newspapers, …
Triplet Censors: Demystifying Great Firewall’s DNS Censorship Behavior
The Great Firewall of China (GFW) has long used DNS packet injection to censor Internet access. In this work, we analyze the DNS …
Assessing the Privacy Benefits of Domain Name Encryption
As Internet users have become more savvy about the potential for their Internet communication to be observed, the use of network …
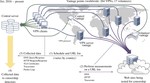
ICLab: A Global, Longitudinal Internet Censorship Measurement Platform
Researchers have studied Internet censorship for nearly as long as attempts to censor contents have taken place. Most studies have …
The Web is Still Small After More Than a Decade - A Revisit Study of Web Co-location
Understanding web co-location is essential for various reasons. For instance, it can help one to assess the collateral damage that …
K-resolver: Towards Decentralizing Encrypted DNS Resolution
Centralized DNS over HTTPS/TLS (DoH/DoT) resolution , which has started being deployed by major hosting providers and web browsers, has …
How Gay Dating Apps Are Being Abused & Used For Entrapment Around The World?
Grindr has been used by gay, bi, and transgender men for over ten years in nearly 200 countries. Gay communities in countries where …
Measuring I2P Censorship at a Global Scale
The prevalence of Internet censorship has prompted the creation of several measurement platforms for monitoring filtering activities. …
An Empirical Study of the I2P Anonymity Network and Its Censorship Resistance
Tor and I2P are well-known anonymity networks used by many individuals to protect their online privacy and anonymity. Tor’s …
同性恋交友应用真的安全吗?研究人员的发现让人有些失望
几天前,我提醒我的妻子我所做的实验完全与性无关,免得她偷瞄我的手机。之后我安装了同性恋交友应用Grindr。我把头像设为一只猫,并且关掉了应用上的“显示距离”选项,这样做能隐藏我的位置。一分钟之后,我打电话给Nguyen Phong Hoang(日本京都的一名安全研究人 …
Renewed Concerns about Privacy on Grindr, Hornet, and Similar Gay Hookup Apps
After claims that Egyptian police used gay hook-up apps to track down gay people and arrest them in 2014 (penalty for same-sex sexual …
Same-Sex Dating App Gives Away Your Exact Location, Even When You Tell It Not To
Three researchers from the Kyoto University in Japan have discovered that three of the most popular same-sex dating apps today are …
Is Your Location Really Private on Grindr? Not Quite...
If someone is truly determined, they can pinpoint where you are by comparing your proximity to fake accounts. Researchers at …
Gay Dating Apps Promise Privacy, But Leak Your Exact Location
A FEW DAYS ago, I warned my wife that the experiment I was about to engage in was entirely non-sexual, lest she glance over my shoulder …
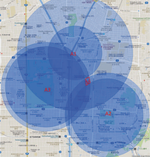
Your Neighbors Are My Spies: Location and other Privacy Concerns in GLBT-focused Location-based Dating Applications
Trilateration is one of the well-known threat models to the user’s location privacy in location-based apps; especially those …
Your Neighbors Are My Spies: Location and Other Privacy Concerns in Dating Apps
Trilateration has recently become one of the wellknown threat models to the user’s location privacy in locationbased applications …
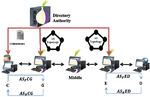
Anti-RAPTOR: Anti Routing Attack on Privacy for a Securer and Scalable Tor
Regardless of Tor’s robustness against individual attackers thanks to its distributed characteristics, the network is still highly …
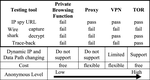
Anonymous Communication and Its Importance in Social Networking
Digital information has become a social infrastructure and with the expansion of the Internet, network infrastructure has become an …
Anonymous Communication and Its Importance in Social Networking
Digital information has become a social infrastructure and with the expansion of the Internet, network infrastructure has become an …